Last year on vacation I took a fishing charter with my family. The boat’s sonar showed us there were many fish in the sea below. We trolled the waters around Grand Cayman, pulling bright and shiny lures that looked like squid to the fish we were after. The trip was mildly successful – we caught one large barracuda — enough to satisfy our fishing hopes for the day and snap some photos.
Cybersecurity professionals call one of the most common cyber threats “phishing.” If you are not familiar with the term, I’m hoping my family’s recent vacation experience will help bring it to life.
The bad guys who phish behave much as my family and I did on the boat. They are not trying to hook a specific person (fish). These individuals (or organizations) are throwing out lures (emails) into a large body of water (the Internet) hoping a fish (you) will bite.
Phishing campaigns somewhat randomly send thousands (or even millions!) of emails.
The campaigns succeed by catching only a few fish. They lure the recipients to:
- Open the email
- Engage with the email by clicking links, responding to the email, or downloading attachments
- Divulge personal or financial information or send money
Please note that while this article refers to phishing emails, the information and discussed here can apply to text messages also. I personally get more and more phishing messages via text. Don’t let your guard down just because a message is on your phone.
Real life examples of phishing and their possible outcomes:
- Basic information request: This phishing campaign seeks sensitive information. Even if they do not get the desired information, any reply may signal they have a “live one” on their line. An information request phishing email may look something like this one I received to my personal email account:
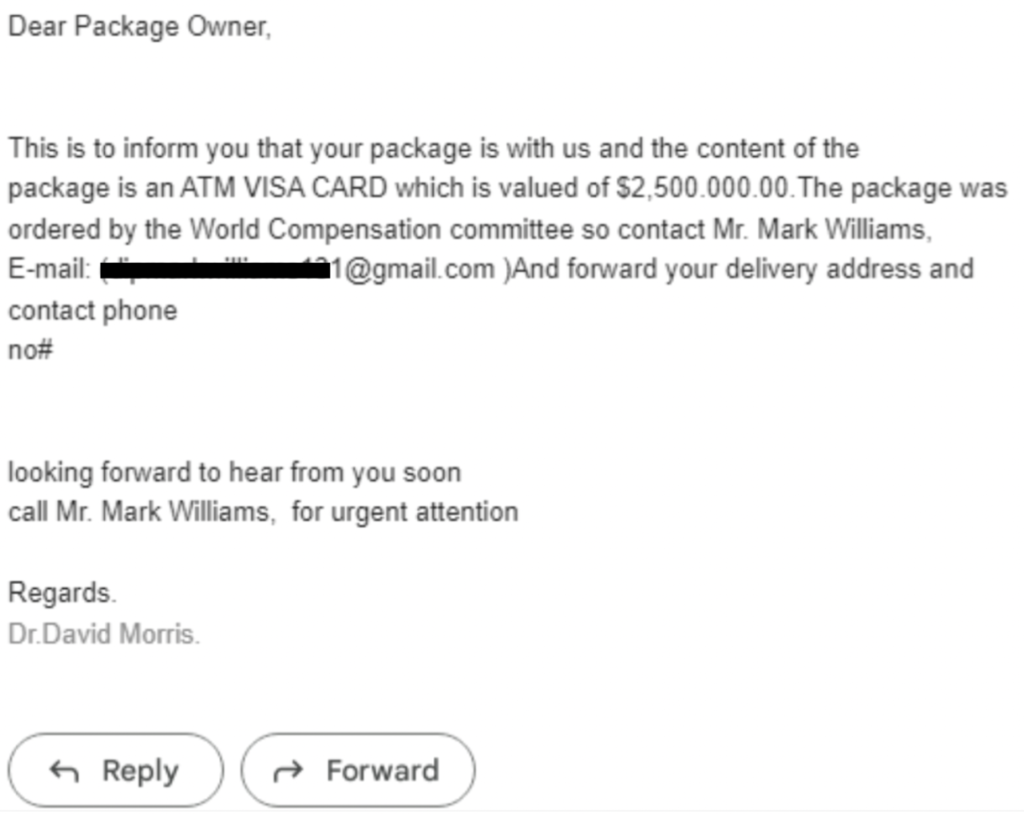
You will notice the scammer did not mention my name, referring to me as Package Owner. Phishing is not targeted to an individual (likely thousands of others received this same email), so they use a generic greeting to address the email recipient.
Had I responded to this email with my address and phone number, the scammers would then be armed with information to attack me with a more sophisticated scheme. Perhaps they would call me and ask for my credit card number so I could pay for the shipping of my $2.5M ATM VISA CARD.
2. Lucrative prize opportunity: Phishing campaigns often send emails that appear to be from sources you recognize. These emails may have familiar logos and look legitimate. Here is one that my email SPAM filter missed:
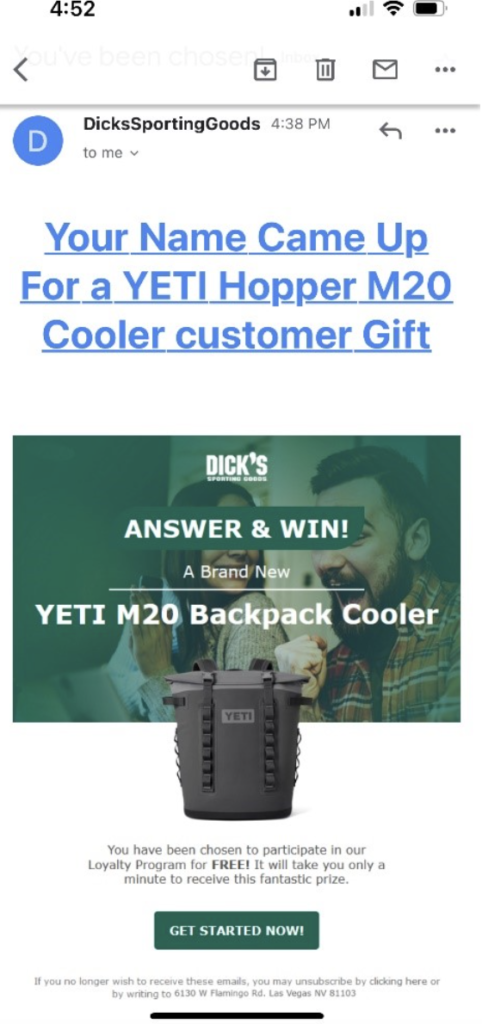
In this scenario, the scammer is attempting to hook me by saying I can win a Yeti backpack cooler if I click the link in the email. However, the link would likely bring me to a fake website. There, they’d ask me for personal information or steal my login credentials which they can sell on the dark web, use to buy things, or try to login to the financial institutions I work with.
3. Download ransomware or other malicious programs to your computer or network: These are very common attacks. The crook sends out emails that include a malicious attachment (or a link) that downloads malware on to your computer and can infect a whole network at a company.
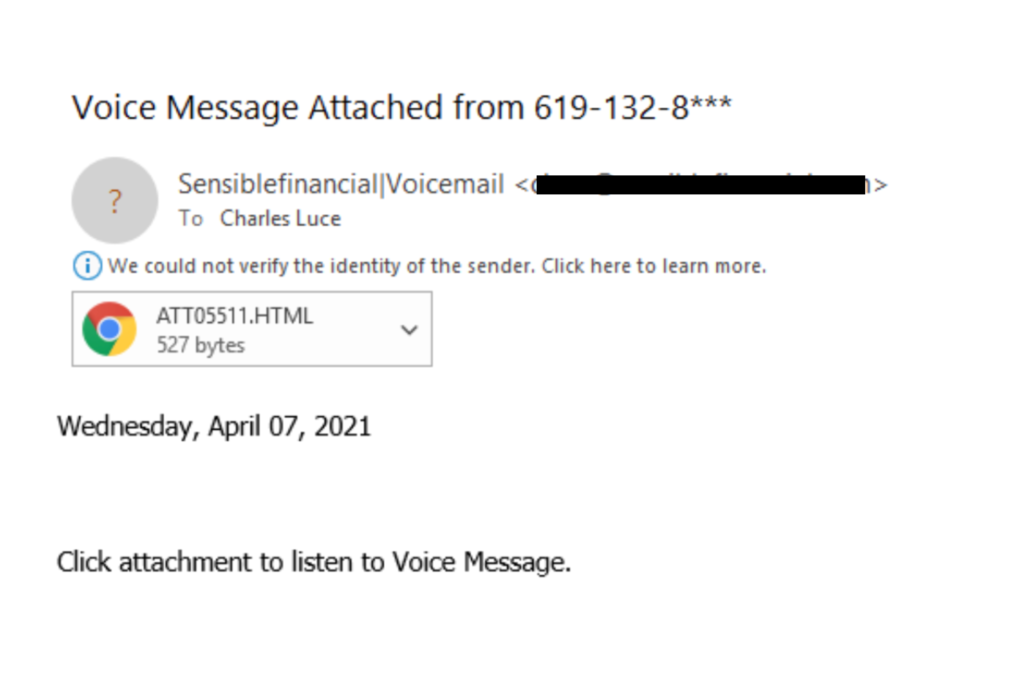
In this example the scammers attached a malicious file to the email. Had I opened that attachment thinking it was a voicemail, it might have infected my computer (if our anti-malware technology did not recognize it as malware). This phishing campaign was a bit more sophisticated than the other examples and may have crossed into the social engineering realm. The crooks customized the sender to look like it was an automated message from within Sensible’s systems (notice the spoofed from email address is Sensible Financial I Voicemail).
How does Sensible protect itself and our clients’ information from hackers?
- Culture: Throughout this series of cybersecurity articles, you will hear us refer to Sensible Financial’s cybersecurity culture. As a group, we talk regularly about cybersecurity and potential threats. During our weekly meetings, we review new phishing campaigns we’ve encountered. When one of us receives a new type of phishing email, we share a screenshot with the whole firm. We encourage everyone to take the extra steps and time to ensure an email is safe before moving forward, even when this slows down our processes.
- Training: Anyone who has just joined Sensible Financial will tell you the first meeting they have with compliance is all about phishing and social engineering. Making this the first topic in a series of compliance and risk meetings for new Sensible people bolsters our cybersecurity and reinforces its importance.
- Testing: Sensible recently ran our own mock-phishing campaign. The mock campaign created a sense of friendly competition and (we hope) kept our people engaged in our cybersecurity initiatives. It also kept us talking about these threats and further strengthened the culture.
- Technology: Culture, training, and testing are important pieces in our cybersecurity program. However, there is a human aspect to all these pieces, and humans are not perfect. Technology is not perfect either. However, it certainly reduces the chances of human error. Therefore, we employ advanced email filtering technologies that capture and quarantine a very large percentage of the phishing emails we receive. Additionally, when a Sensible professional clicks a link in an email, the technology analyzes it before allowing the link to open. The software will not allow any links it identifies as unsafe to open.
How can you protect yourself from phishing emails and texts?
- Scrutinize, scrutinize, scrutinize: Never respond to, or engage with, emails requesting sensitive information. Take special care with emails from people or companies you are not familiar with and emails asking you to reset your password, or login from a link. Never click links, or download attachments, from senders you do not trust 100%. If you are unsure a link is authentic, bypass the email and type the company’s website into your browser
- Learn to spot phishing : Any email asking for personal information is a red flag. Additionally, emails addressing you as sir, madame, customer, client, etc. are questionable. In an upcoming social engineering article, you will learn how to examine more sophisticated emails addressing you by name. Emails with misspellings, odd language, and company logos that are a bit off are also red flags. Watch out for unsolicited requests to reset your password as well.
- Take advantage of standard technology: You are most definitely already under daily attacks from phishing campaigns. If you have not seen many in your inbox, it’s likely because your email provider has automatically filtered them. Providers like Gmail have preset SPAM filtering technology applied to your account. You can report phishing emails that sneak past these filters as SPAM to your provider. Over time, the provider’s software learns about the SPAM you receive and catches more phishing emails.
- Research advanced technology: Companies like Sensible employ sophisticated email and malware protection. You can also purchase software to use for your personal accounts and devices. Webroot, Norton, Bitdefender, and Malwarebytes (among others) are well known and have affordable internet security and antivirus packages for corporations and individuals.
- Be proactive:
- Consider freezing your credit reports at the three credit agencies, Experian, TransUnion, and Equifax. You can do this online. You will need to create a login account at each agency. If you want to apply for a loan in the future, you simply login and unfreeze your credit until the lender is finished running your credit. Then re-freeze.
- Use a reputable password manager to create strong passwords and change passwords that may have been compromised.
- Review your financial transactions often. You can set up automatic alerts from your financial institutions to notify you whenever there is activity in your accounts.
- Download one of the free credit monitoring apps. Additionally, many credit card companies work with credit monitoring technology firms, and they offer you this service at no additional cost. These won’t stop an event. However, they might discover something sooner than you would without them.
*FULL DISCLOSURE: Chuck Luce, Sensible Financial’s Chief Compliance Officer & Associate Director of Business Operations, and Sensible Financial are not cybersecurity experts. This article is not intended to fully educate readers on all aspects of phishing threats, cyber threat protection, or cybersecurity. Please talk to your advisor if you have any questions or concerns about keeping your digital information safe and we can point you to some helpful resources. Here is a great place to start.
All written content is provided for information purposes only. Opinions expressed herein are solely those of Sensible Financial and Management, LLC, unless otherwise specifically cited. Material presented is believed to be from reliable sources, but no representations are made by our firm as to other parties’ informational accuracy or completeness. Information provided is not investment advice, a recommendation regarding the purchase or sale of a security or the implementation of a strategy or set of strategies. There is no guarantee that any statements, opinions or forecasts provided herein will prove to be correct. Past performance may not be indicative of future results. Indices are not available for direct investment. Any investor who attempts to mimic the performance of an index would incur fees and expenses which would reduce returns. Securities investing involves risk, including the potential for loss of principal. There is no assurance that any investment plan or strategy will be successful.